Cooperative driving maneuvers expand fully-automated driving with maneuver options, that are not available in current traffic. The reliance on a common plan allows for smaller safety distance, efficient overtaking maneuvers and optimized evasive maneuvers in an emergency situation. On the downside, car-to-car-communication (Car2Car communication) opens up new possibilities for targeted cyberattacks.
With the diverse set of partners in the initialization project “Connected Mobility” as part of the Profilregion Mobilitätssysteme Karlsruhe(“Profilregion: High Performance Center for Mobility Research”), those new hacking methods are analyzed from different perspectives. To demonstrate the problem, the group of researchers initially developed a hacking scenario example on the group formation process, which takes place at the beginning of each cooperative driving maneuver. Currently, the partners are working on applicable countermeasures to prevent such cyberattacks.
The partners
The partners of the cyberattack scenario are:
- Institute for Information Processing Technologies (Institut für Technik der Informationsverarbeitung – ITIV): Simulation and architecture of hardware-oriented Car2X communication
- The Competence Center for Applied Security Technology (Kompetenzzentrum für angewandte Sicherheitstechnologie – KASTEL): Analysis of misuse cases in software, especially by cyberattacks
- Department of Measurement and Control (Institut für Mess- und Regelungstechnik – MRT) and Research Center for Information Technology (Forschungszentrum Informatik – FZI): Implementation, analysis and test of maneuver planning and control algorithms
- Fraunhofer Institute of Optronics, System Technologies and Image Exploitation (IOSB): Algorithms for group and alliance formation for cooperative maneuvers, kooperative maneuver planning and automotive simulation
The initial situation
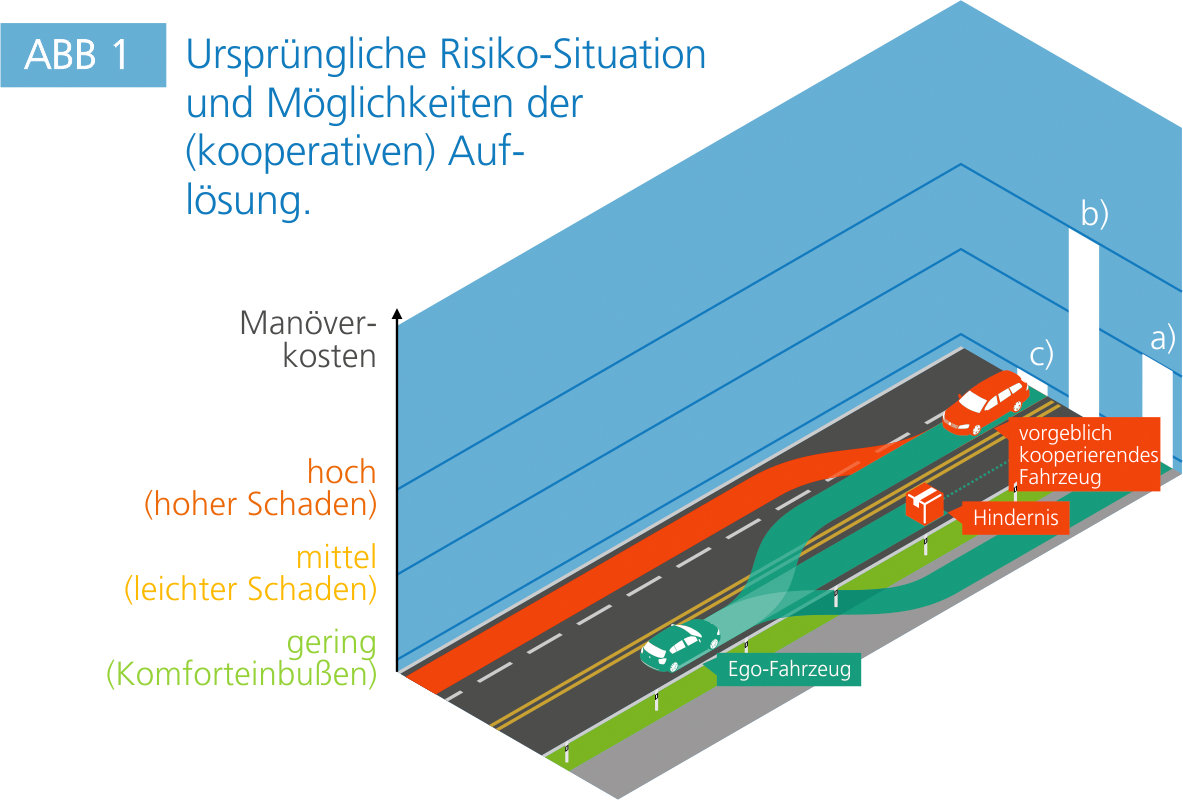
The particularity of the developed scenario is given by the new type of attack, which in this case does not require access to any automated vehicle or infrastructure, but instead just malware installed on the driver's smartphone (or some other carried-along broadcasting device). This thus leads to a potentially high diffusion of the attack-vector onto a wide mass of vulnerable traffic participants and situations. The analyzed scenario includes a fully-automated vehicle steered by an artificial intelligence (green vehicle) and an oncoming vehicle with a human driver (red vehicle).
The malware
The function of the malware is to utilize the Car2Car communication channel to other (automated) traffic participants, and falsely identify the victim’s car as a cooperative automated vehicle. To counteract the premature discovery as malicious software, the malware analyzes the driving situation using GPS, accelerometer information and map data, and initially declines any cooperation request properly. Only in the case of a potentially dangerous situation, the malware accepts and confirms the requested cooperative maneuver. The malware's objective is to provoke such maneuvers of fully-automated vehicles, that their artificial intelligence would not have classified and executed as safe maneuvers without the (assumed) cooperation of other vehicles. However, as the human driver has no knowledge of the planned cooperative maneuver, a high-risk situation with an inevitable accident is very probable to occur.